Receive Your Complimentary Assessment
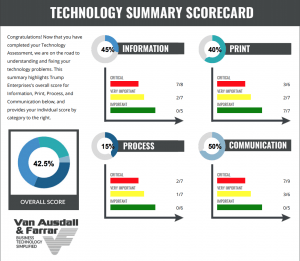
Knowing your score helps you understand how technology can improve your business and where you should focus your attention. This assessment will help you understand what you need to eliminate, what you need to optimize, and how you need to leverage improvements to grow your business.
The assessment takes only 10-15 minutes.
